Ubuntu 22.04 is shipping with Wayland as the default communication protocol for the display server, replacing the old and X11 (X Window System).
Interestingly although Firefox is supporting Wayland natively, the default stable Firefox snap package doesn’t use it. I is still using XWayland as compatibility layer.
How to check if Firefox is using Wayland or X11?
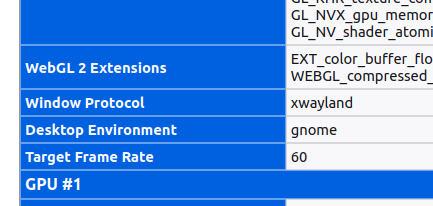
Open:
about:supportand search for `Window protocol`
Window Protocol xwaylandThat is intentional, see
https://bugzilla.mozilla.org/show_bug.cgi?id=1631462#c21
So what about Firefox Beta? To install Firefox Beta snap next to Firefox stable, see the earlier blog-post Install seperate Fiefox Beta snap.
Open
about:supportAnd search for `Window protocol`
Window Protocol wayland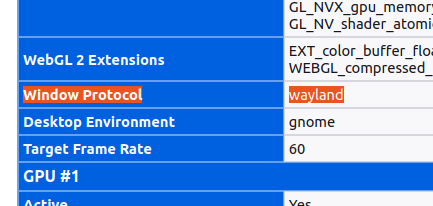
Note the missing X, that means Wayland is used as the communication protocol.
Why doesn’t show Wayland in the User-Agent header of Linux browsers?
To check the the User-Agent in Firefox Beta, navigate to something like a ip-address checker:
Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/109.0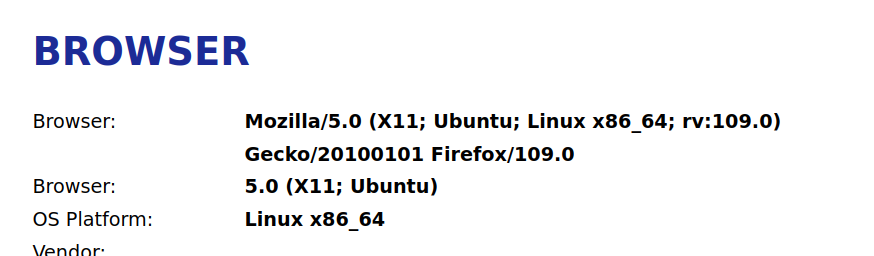
Although X11 is not used, it still shows X11. I wonder if that is intentional? Probably that is. User-Agent strings are hampered by historical mistakes, like browser-sniffing.
And setting a detailed User-Agent is also a privacy and security risk. Giving to much and unnecessary information about your system. So it is about limiting exposure to browser-fingerprinting.
Be aware this sucks, once you’re aware there is market-power in user-agents. The major players make the rules of the game.